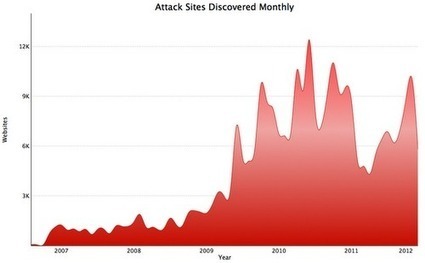
Faced with external security threats from hackers and others, along with a growing array of even more dangerous internal security threats, companies worldwide are feeling the heat.
Organizations traditionally have had only two options to address identity and access management:
1. Internal excessive privilege - System Administrators with complete access to servers and data can pose a tremendous internal threat if they turn against the company. Similarly, everyone from admins up to executives poses a threat to security and data if they maintain excessive access rights after changing positions or taking on different roles.
2. Third party access - Giving partners and other third parties appropriate access to data is no longer cut and dried. Data stored in the cloud may be located across the country or overseas—or sit on physical servers owned by one vendor, but housed in facilities owned by any number of data centers. Employees of these third parties often have direct access to unencrypted data, or they may retain copies of both encrypted or unencrypted data.
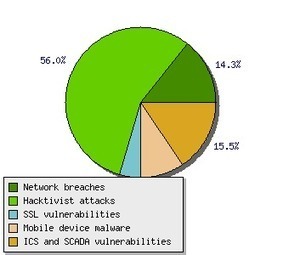
3. Hacktivism - Politically motivated hacking is on the rise. Members of various groups assert that much of their success comes not from their technical expertise, but from having found easy targets. While an organization may not have control over whether or not it is attacked, effective identity and access management strategies and technologies, and basic employee security training, will reduce the chances that attacks will succeed.
4. Social engineering - Social engineering is the age-old technique of using lies, deception and manipulation to gain sufficient knowledge to dupe an unwary employee or company. Using public social channels to detail every aspect of your upcoming “unplugged” vacation trip may be just what a scammer needs to put an attack in motion.
5. Internal negligence - Negligence typically is an offense committed by management when “they should have known better.” Most successful data security breaches have some element of managerial negligence associated with them, such as simply forgetting to check log reports for clearly suspicious patterns.
Gust MEES: A MUST READ for Education and Business!
Read more:
http://www.net-security.org/secworld.php?id=13084&utm_source=dlvr.it&utm_medium=twitter



 Your new post is loading...
Your new post is loading...






![How to Avoid 17 Internet Scams [INFOGRAPHIC] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/rAUu9hiWLA6h_bZS-utdfTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)















Is ti possible that we have a special room for this?
More information on BYOD